How can an enterprise today more effectively protect AD (Active Directory)? This is a relevant question for those managing network security. Research giant Forrester noted, “Having a strong control of privileges in an ever-evolving company is critical and one of the challenges that every CISO must tackle.”
Even so, Forrester stated that “100% of corporations suffering from cybersecurity breaches had a security policy.” Simply put, it takes more than rigid controls, audits and security policies to defend AD properly. This is a realization not lost on Fremont, Calif.-based Attivo Networks.
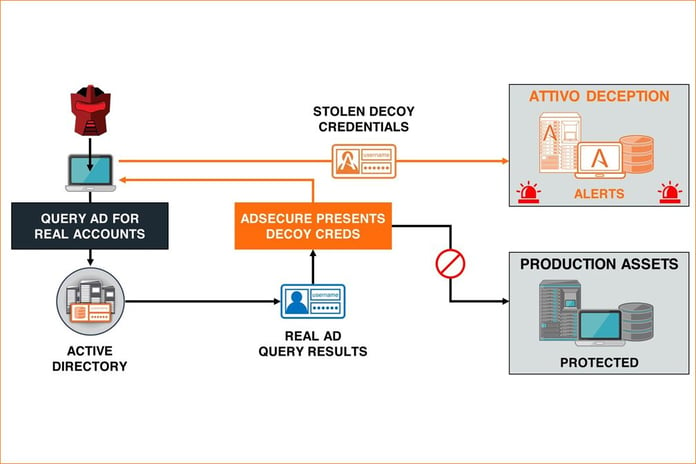
Attivo’s ADSecure has a unique take on protecting AD; it uses the age-old art of deception with an added twist of concealment. ADSecure is designed to deceive even the most aggressive intruders with decoys and other techniques rooted in the world of deception.
[To see a larger version of the image at upper left, right-click on it and select “View Image.”]
While the concept of “deception” often creates an unfavorable mental image for most people, the truth is that “deception” and its sibling “concealment” are powerful tools that can protect enterprises from even the most aggressive cyberattackers.
ADSecure breaks out from the traditional approach to deception that is found in the company’s other products to protect IT assets, data and intellectual property from the ills of the cyberattacker community. Instead of laying decoy traps and obfuscating the bait among real credentials or artifacts, the company has instead chosen simply to deny the attacker the ability to see and touch AD altogether.
Perhaps the most important thing to remember about AD is that any account compromise could lead to handing the proverbial keys of the enterprise castle to an intruder. Once AD is compromised, attackers may be able to leverage lateral attacks, steal other credentials, access numerous systems or even bring the whole network to a locked state, where no one but the attacker can access corporate assets.
What better way is there to derail this form of an attack than to hide and deny their access? What if you could do this and return fake data that steers the path of the attackers into decoys that trick them into spilling their tactics and methods?
A Closer Look at Attivo’s ADSecure
ADSecure brings together numerous security capabilities to protect AD from compromises. At its most basic level, the platform detects unauthorized queries to AD. It reduces the risk that those queries present by misdirecting attackers to decoys, protecting legitimate AD objects from exposure and compromise. Ultimately that reduces the attack surface of AD.
What’s more, by misdirecting attackers into a deception environment, the platform can safely gather TTPs (tactics, techniques and procedures), which can be used to develop threat intelligence, provide forensics and create an accelerated response.
Of course, there is much more to ADSecure than just confusing attackers. The platform also tracks attackers (and attacks), provides visibility to administrators and supports proactive threat hunting. It is also worth noting that ADSecure accomplishes its objectives without altering production AD controllers. In other words, it can return deceptive objects without disrupting production AD environments.
Hands-On with ADSecure
- ADSecure can be a stand-alone module of the ThreatDefend platform or part of an ecosystem of threat protection products available from Attivo, which function under the Attivo Networks ThreatDefend Detection and Response Platform. ADSecure deploys as a module to the ThreatDefend platform, which makes installation quite straightforward. Once installed, ADSecure can be managed through a stand-alone management console or become fully integrated into the ThreatDefend platform, where it adds new features to the management consoles and administrator dashboards.
- ADSecure can operate independently, or for organizations that would like the benefit of engaging the attacker for counterintelligence, it works hand in hand with Attivo’s BOTsink deception server, which is part of the ThreatDefend platform. The BOTsink houses the network decoys and manages the deception environment. ADSecure actively works on the endpoint to detect imposter AD queries and then directs those queries to the deception environment, where decoys are used to defuse an active attack. What’s more, the deception environment records the activity and alerts administrators of the attempted compromise. The BOTsink is the glue that makes deception work and engages with the attacker when paired with ADSecure.
- The primary administrator dashboard is built around the real-time activity presented by the BOTsink deception server. The dashboard offers an “at-a-glance” status of network activity, showing the severity of detected events, as well as the types of attacks detected. The dashboard also provides additional insight into the recent events, as well as the top targets on the network. Administrators can drill down to garner more information on the displayed elements.
The dashboard also provides alerts of suspicious events. In this case, the dashboard is displaying that someone attempted to gain access via AD to a resource on the network, and that the platform diverted the attempt for privilege escalation by providing a deceptive credential to the intruder. All critical information surrounding the attempted compromise is recorded, providing information for forensic analysis.
Conclusions
Perhaps the best analogy for ADSecure is to think of the module as a silent guardian that obstructs attacks by confusing the attacker with legitimate-looking information that is actually a fantasy. Or more simply put, ADSecure employs a magician’s sleight of hand to send attackers on what is the digital equivalent of a wild goose chase.
The importance of protecting Active Directory in today’s cloud-enabled world cannot be underestimated, as noted by cybersecurity experts.
“Cybersecurity professionals continue to witness cybercriminals target Active Directory for privilege escalation, lateral movement and reconnaissance activities. Accounts and information stored in Active Directory are often targeted during security breaches because credential leverage is a necessary and invaluable aspect of every compromise. Solutions that detect and defend against Active Directory-related attacks are an important part of any security program,” said Marshall Heilman, senior vice president of Managed Defense and FLARE at Mandiant.
For those looking to better protect Active Directory (and the resources it provides to users), the paradigm of deception proves to be quite valuable. ADSecure handily brings concealment and deceptive techniques to the forefront of protection and makes adoption quite easy. As a stand-alone product, companies can reduce the risk of lateral movement and privilege escalation. When used within Attivo’s ThreatDefend platform, it brings forward a unified way to protect networks from a number of different threats, beyond just those applicable to Active Directory.
Arguably, the most important capability of ADSecure is how it can detect and prevent lateral attacks. For example, if an attacker attempts to harvest Active Directory data, ADSecure responds by providing the attacker with what looks like meaningful information but is, in fact, false data. Meanwhile, the attacker believes that they have successfully gathered critical information, yet that information is useless, and all details of the attack have been recorded, without the attacker even knowing. But there is much more to ADSecure than defending against lateral attacks. The module also can identify if stolen credentials are being used, which is becoming a growing problem as more and more workers shift to home or remote workplaces.
In the past, compromises impacting Active Directory and the harvesting of Active Directory data were a major concern for organizations using AD. Yet, there was really no effective way to automate the protection of AD, and it was very difficult to detect the theft of AD data, if not impossible. It was a weakness amplified by the introduction of cloud services and resources that were also dependent upon AD. ADSecure effectively brings automated protection to Active Directory, which was once thought impossible.
Frank Ohlhorst is a veteran IT product reviewer and analyst who has been an eWEEK regular for many years.